zHeros
Diaries
"Analysing the itsy bits of Cybersecurity Technologies. A topic at a time, a tool at a time."
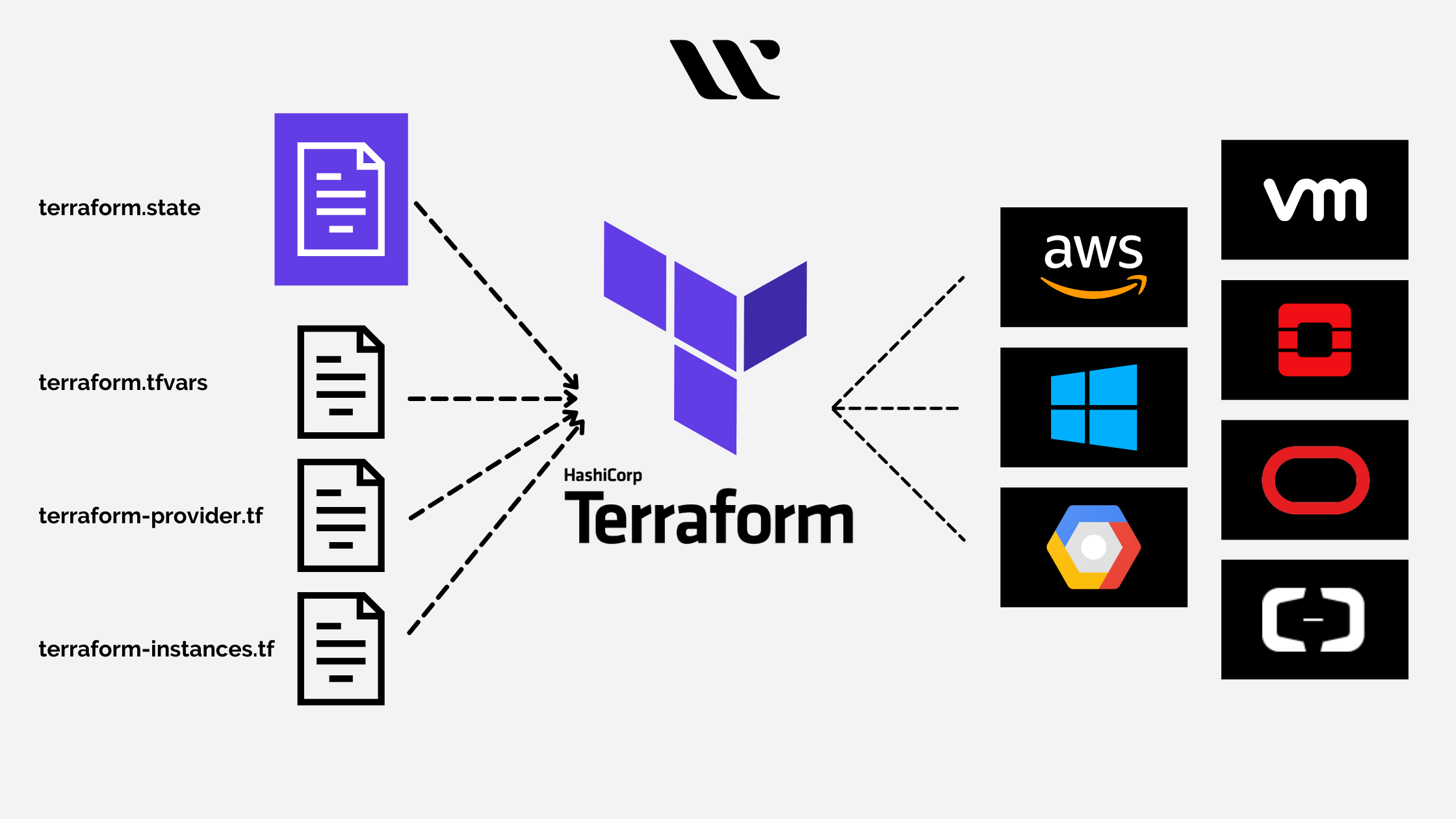
Terraform
Automating Infrastructure as a Service (IaS). Terraform uses the HCL, Hashicorp language to write
clear configuration .tf or .tf.json files.

SIEM
Security Information Event Management, Cutting edge technology for
centrally managing security events. SIEM aggregates and parse data into indexes
to make searching for events efficients.
Navigating Time Synchronization in Linux
NTP, PTP, Chrony, and NTPsec Explained. The Network time protocol is esseantial in modern
computing, it's enables seamless communication among applications, makes log efficient
log analysis possible, plays a critical role in financial market and many more.